Backofficer Friendly
Nutter offers up resources and advice to an IT pro considering implementing a honeypot It’s been a challenge to keep all the patches/updates applied to our servers. We’ve been looking for something we can use as an additional layer of protection. I’ve been reading about using a honeypot, but I’m not sure which way to go. What are our options? - Via the Internet This is a deep subject that will take more room than I have here, but I’ll give you some places to get started.
Books.google.de - Information Security and Ethics: Concepts, Methodologies, Tools, and Applicationsserves as the ultimate source on all theories and models associated with information privacy and safeguard practices to help anchor and guide the development of technologies, standards, and best practices to meet these.

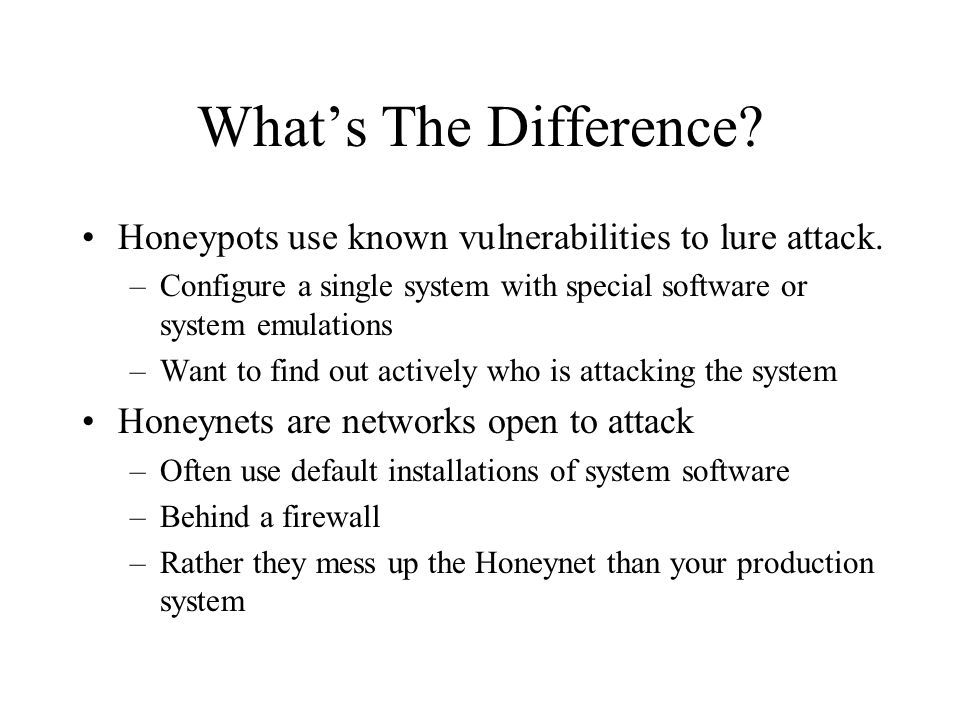
The first thing I would do is check with your corporate attorney to see what the laws/regulations are in your state and or at the federal level before turning up a honeypot. If your attorney doesn’t specialize in subjects dealing with the Internet, find one who does and check with the person periodically to ensure you stay out of harm’s way in the legal area. Having said that, there are several ways you can implement a honeypot. A basic Windows-based honeypot called Back Officer Friendly is available from. They also have a Linux version available.
A more robust honeypot by the name of Specter that can emulate different operating systems and more services than Back Officer Friendly is available from. If you’re comfortable working with Linux, honeyd may be something you should look. Available at, this is one of the more popular honeypot options available. This is just the start of implementing a honeypot. You also have to think about whether to put it inside and/or outside the firewall.
There are several different Web sites, such as honeyd.org, that you can go to for information. Bigfish Columbus Ghost Of The Mystery Stone. I also suggest getting a copy of Lance Spitzner's book, 'Honeypots: Tracking Hackers.'